نکته: امضاهای مفقود شده تنها زمانی رد میشوند که گزینه اجبار امضای SDK فعال و روشن باشد.
چرا باید از قابلیت امضای SDK متریکس استفاده کرد؟
هرچند که SDK متریکس با استفاده از کانالهای ارتباطی رمزنگاری شده نظیر HTTPs با سرورهای متریکس در ارتباط است، اما این دادهها قابلیت ویرایش و خوانده شدن از سوی متقلبان را دارند. این اطلاعات استخراج شده طی یک «حمله» میتواند برای ایجاد نصبهای غیرواقعی و جعلی مورد استفاده قرار گیرد. درست در همینجاست که امضای SDK متریکس به کمک شما خواهد آمد.
امضای دیجیتال یا digital signature چیست؟
امضای دیجیتال یا digital signature یک مدل ریاضی است که برای اعتباربخشی به پیامها یا اسناد دیجیتال به کار میرود. از نظر طراحی، یک امضای دیجیتال نمایانگر این است که پیام در امنیت کامل منتقل شده است و هیچ اطلاعاتی از آن در جریان فرآیند انتقال در معرض تغییر نبوده است .هنگامی که پیغامی از کانالی ناامن ارسال میشود، یک امضای دیجیتال در صورتی که به شکل صحیح استفاده شده باشد میتواند برای شخص گیرندهی پیام، سند معتبری باشد تا ادعای شخص فرستنده را باور کند.به عبارت بهتر، شخص گیرنده از طریق امضای دیجیتال میتواند این اطمینان را حاصل کند که همان شخص فرستنده آن سند را امضا کردهاست و پیام مورد نظر جعلی نیست.
امضای SDK چیست؟
امضای SDK نیز یک رشتهی متنی است که در تمام ریکوئستهایی که از SDK متریکس به سرورهای متریکس فرستاده میشود، قرار میگیرد. در این روش، SDK یک امضا را از روی رمز اپ (مقداری که تنها در اختیار ناشر اپلیکیشن و متریکس است) محاسبه میکند و به سرورهای متریکس این امکان را میدهد که صحت تمامی نصبهای آتی اپ را تأیید و تصدیق کنند. به این شکل که اگر این امضای تولید شده با امضای ریکوئست یکی باشد، ریکوئست قبول میشود و در غیر این صورت، آن ریکوئست جعلی تشخیص داده میشود.
اگر فرد متخلف دادههای مهمی (مانند زمان نصب یا شناسههای دستگاهها) را که در طول یک نصب ارسال میشود سرقت کند سروهای متریکس آنها را شناسایی و نصب مورد نظر را به عنوان نصب تقلبی لحاظ میکند.
رمز اپ یا App Secret چیست؟
رمز اپ یا App Secret مجموعهای از 5 عدد است که متریکس از این مقادیر برای رمزدار کردن دادههای کلیدی و خاص به هنگام ارسال ترافیک SDK به سرور متریکس استفاده میکند؛ یعنی جایی که متریکس میتواند صحت نصبها را بر اساس این مقدار رمزشده تأیید کند. نکته مهم و اساسی در مورد رمز اپ این است که این پارامتر حتماً باید در قالب و فرمت متنی ساده plain text (دقیقاً به همان صورتی که از داشبورد متریکس دریافت میکنید) استفاده شود.
توصیه ما برای اثربخش بودن بیشتر، این است که برای هر یک از موارد زیر یک رمز جدید ایجاد کنید:
- پلتفرمهای متفاوت (iOS، اندروید و غیره) و
- انتشار هر ورژن جدید از اپلیکیشن
در Metrix blog فیچر امضای SDK را معرفی کردهایم.از لینک زیر بخوانید:
قابلیت دیگری در متریکس: امکان امضاکردن کیت توسعه نرمافزار
راهنمای استفاده از قابلیت امضای SDK یا SDK Signature
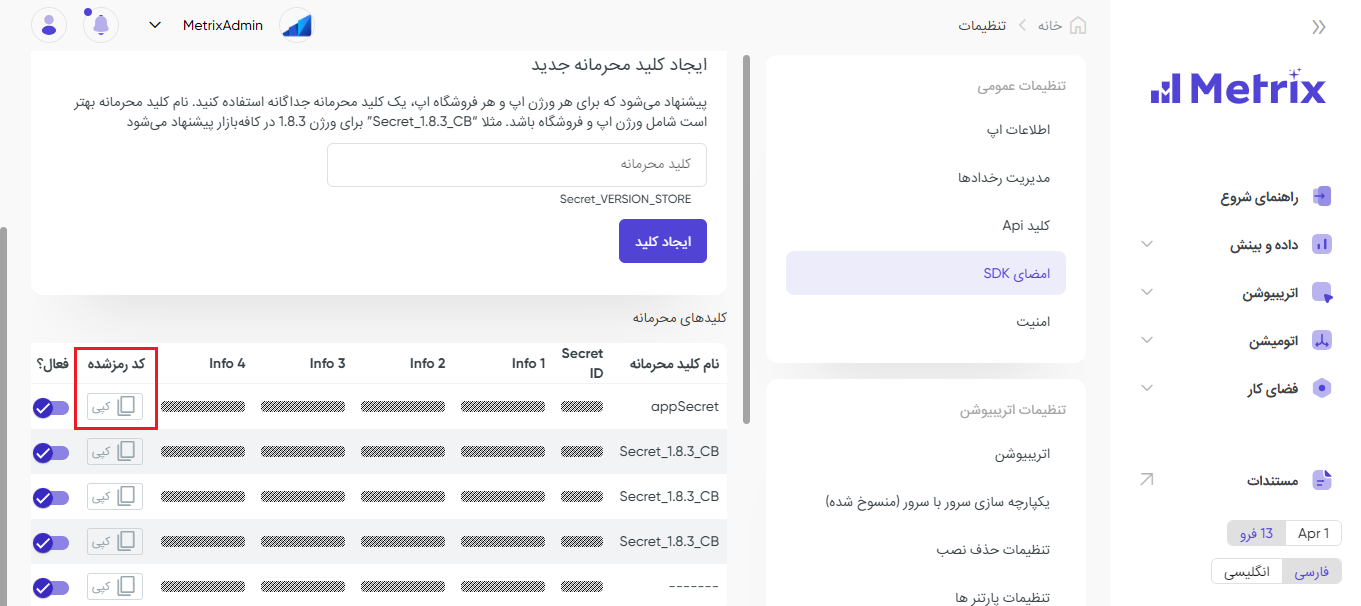
از منوی سمت راست پنل، وارد بخش فضای کار> تنظیمات شوید؛ سپس از بخش “تنظیمات عمومی”، “امضای SDK” را باز کنید.
در اینجا شما میتوانید امضای SDK را فعال کنید.
شما با فعالسازی قابلیت SDK Signature در پنل خود و دریافت شناسه مخصوص به خودتان، امنیت ارتباط و انتقال اطلاعات را افزایش داده و از سلامت آمار اپلیکیشن خود اطمینان بیشتری حاصل میکنید.
پس از فعالسازی SDK signature در پنل خود، از ستون Encoded یا کد رمزشده ، شناسه مربوط به signature را کپی و طبق مستندات پیادهسازی SDK متریکس، آن را داخل تنظیمات اپلیکیشن خود قرار دهید.
در Metrix blog به طور کامل قابلیت امضای SDK را معرفی کردهایم. میتوانید از لینک زیر آن را بخوانید:
قابلیت دیگری در متریکس: امکان امضاکردن کیت توسعه نرمافزار
Frequently asked questions
1. چطور میتوانم یک رمز اپ پیاده سازی کنم؟
هنگامی که رمز اپ خود را ایجاد کردید، آن را به همراه شناسه رمز اپ (App Secret ID) به دولوپر تیم خود بفرستید تا پیادهسازی را انجام دهد. دستورالعمل پیاده سازی را از بخش مستندات بخوانید.
2. دادههای مربوط به امضای SDK چطور در داشبورد من ظاهر می شوند؟
نصبهای تقلبی در بخش “شناسایی تقلب” در پنل متریکس نمایش داده میشوند. نصبهایی که به دلیل داشتن امضای غیر معتبر رد شده محسوب میشوند تحت عنوان untrusted devices ظاهر میشوند.
3. تفاوت میان یک امضای نامعتبر و یک امضای ناموجود (missing signature) چیست؟
یک امضا زمانی نامعتبر است که با امضایی که متریکس بر اساس رمز اپ شما محاسبه میکند همخوانی نداشته باشد. این نوع امضاها دربردارندهی امضاهای تقلبی و امضاهایی است که از رمز اپهای غیرفعال شده محاسبه شده باشند.
اما امضای missing هنگامی است که یک نصب اپلیکیشن بدون هیچ امضایی به سرور برسد. نصبهای بدون امضا تنها درصورتی رد خواهند شد که گزینه SDK Signature enforcement یا اجبار برای امضای SDK فعال و روشن باشد.
4. چطور میتوانم از نصبهای مردود در ترکر متریکس باخبر شوم؟
در صورتی که یک نصب به دلیل امضای SDK نامعتبر یا مفقود شده، مردود و تقلبی اعلام شود میتوانید از طریق سیستم کال بک در لحظه (real-time callback) متریکس مطلع شوید. برای اینکه دلیل یک نصب تقلبی یا اتریبیوشن مجدد تقلبی را دریافت کنید {rejection_reason} را به کال بک نصب تقلبی خود اضافه کنید. نحوه استفاده از قابلیت کالبک متریکس را در بخش “راهنمای کاربران” به صورت کامل توضیح دادهایم.
درصورتی که یک نصب به دلیل امضای SDK نامعتبر یا ناموجود (missing) رد شده و تقلبی محسوب شده باشد چنین پیامی را از طریق کال بک دریافت خواهید کرد:
rejected_install_reason=invalid_signature
برای دریافت کالبکها در لحظه (real-time calback) به روش زیر عمل کنید:
در داشبورد متریکس:
- در پنل متریکس از منوی سمت راست، بخش اتریبیوشن>کالبکها را باز کنید.
- آیکون ویرایش را در کنار rejected install را انتخاب کنید.
- آدرس (URL) خود را وارد کنید و یک جفت مقدار را به صورت کلید برای دلیل رد نصب اضافه کنیدa. یک کلید از انتخاب خود وارد کنید: این کلید میتواند متناسب با تنظیمات سرور خودتان باشد
b. مقدار مورد نظر باید {rejection_reason} باشد
c. مثال: rejected_install_reason={rejection_reason}
- گزینه update یا به روز رسانی را انتخاب کنید.